#
ART OF OSINT : Whispers of the Web

#
What is OSINT ?
Open-Source Intelligence (OSINT) refers to the practice of gathering, analyzing, and using publicly available information to make informed decisions. Unlike covert or classified sources, OSINT draws on publicly accessible data from various mediums such as websites, social media, news outlets, and public databases. Its primary goal is to collect actionable intelligence that can be utilized for security, competitive intelligence, strategic planning, and other purposes.
#
Who Uses OSINT?
OSINT tools and techniques are used by a diverse range of individuals and organizations, including:
- Law Enforcement – To investigate criminal activities and track criminal networks.
- Intelligence Agencies – For gathering foreign and domestic intelligence.
- Military – To support operational planning and monitoring adversaries.
- Business and Competitive Intelligence – To monitor competitors and market trends.
- Cybersecurity Professionals – To identify threats and vulnerabilities.
- Journalists – To uncover stories, track sources, and verify information.
- Researchers – For academic purposes and in-depth analysis.
- Criminals – To exploit publicly available data for illicit activities.
- Everyday Individuals – To gather information for personal, professional, or academic reasons.
#
OSINT in Law Enforcement: Tracking Criminal Networks
#
Law Enforcement and OSINT
OSINT is a critical tool for law enforcement agencies investigating criminal activities. One common application is tracking gang activity and organized crime through public sources such as social media, blogs, and other online platforms. Some key areas where OSINT is used by law enforcement include:
- Monitoring Gang and Criminal Groups: Law enforcement uses OSINT to track gang affiliations, activities, and locations, often identifying members through tattoos, social media profiles, and public interactions.
- Investigating Crime Scenes: Social media posts can provide investigators with crucial evidence, such as photos, videos, or location tags, which may be used to piece together timelines, connections, and motives.
- Gathering Evidence for Prosecutions: Suspects often inadvertently incriminate themselves by posting about their criminal activities online. This can provide investigators with vital leads.
- Public Appeals: OSINT tools are used to locate witnesses, share wanted posters, or request public assistance through social media and online platforms.
#
Criminal Use of OSINT
While OSINT is predominantly used for legitimate purposes, it is also exploited by criminals. For example, organized crime groups—such as Mexican cartels—have been known to use social media and other public platforms to gather information for extortion schemes. In 2019, USA Today reported that cartel members used social media to identify and target the families of kidnapped victims, demanding ransom payments based on publicly accessible data.
#
Careers in OSINT (Open-Source Intelligence)
As the demand for information gathering, cybersecurity, and data analysis continues to rise, careers in OSINT are becoming increasingly important across various sectors. OSINT professionals play a key role in collecting, analyzing, and utilizing publicly available information to support decision-making, investigations, security operations, and more. Below are some of the key career paths in OSINT:
#
OSINT Analyst
- Role: OSINT Analysts are responsible for gathering, analyzing, and interpreting publicly available information to provide actionable intelligence. They use a variety of open-source tools to monitor social media, websites, forums, and databases, looking for patterns, trends, and threats.
- Key Skills:
- Strong analytical and research skills
- Proficiency with OSINT tools (e.g., Maltego, Shodan, Spiderfoot)
- Familiarity with social media platforms and data scraping
- Ability to synthesize data and create reports
- Industries: Intelligence agencies, law enforcement, cybersecurity firms, private investigation companies, media outlets.
#
Cybersecurity OSINT Specialist
- Role: A Cybersecurity OSINT Specialist uses open-source intelligence to identify and assess potential cyber threats, vulnerabilities, and threats in the online environment. They track threat actors, analyze tactics, and monitor emerging security issues.
- Key Skills:
- Knowledge of cybersecurity concepts and tools (e.g., firewalls, intrusion detection systems)
- Experience with OSINT tools for threat hunting and reconnaissance
- Familiarity with the dark web and underground forums
- Industries: Cybersecurity firms, government agencies, private sector, financial institutions.
#
Digital Forensics Expert
- Role: Digital Forensics Experts use OSINT to investigate cybercrimes, collect evidence from digital devices, and help law enforcement solve criminal cases. They may gather and analyze data from social media profiles, websites, emails, and other publicly accessible sources.
- Key Skills:
- Expertise in digital forensics tools and techniques
- Understanding of legal and ethical considerations in digital investigations
- Ability to trace online activities and analyze digital footprints
- Industries: Law enforcement, government agencies, private investigation firms, legal firms.
#
Threat Intelligence Analyst
- Role: A Threat Intelligence Analyst focuses on gathering and analyzing information from open sources to identify and evaluate potential threats, whether they be cyber-attacks, terrorism, or criminal activities. They synthesize OSINT to predict and mitigate risks.
- Key Skills:
- Knowledge of global threat landscapes and emerging risks
- Experience with OSINT tools and databases (e.g., VirusTotal, Recon-ng)
- Analytical thinking and ability to create threat reports
- Industries: Government intelligence agencies, private security firms, multinational corporations, military.
#
Intelligence Officer/Analyst (Government & Military)
- Role: Intelligence officers or analysts in government or military organizations use OSINT to monitor geopolitical events, track adversary activities, and assess national security threats. They help shape policy and inform operational decisions based on publicly available data.
- Key Skills:
- Knowledge of intelligence gathering and analysis techniques
- Proficiency with OSINT collection tools and methods
- Understanding of geopolitics, military affairs, and security policies
- Industries: Government agencies (CIA, NSA, MI6, etc.), military, defense contractors.
#
Journalist / Investigative Reporter
- Role: Journalists use OSINT to research stories, verify information, and find sources. Investigative reporters use public records, social media, websites, and other open sources to uncover hidden details, expose corruption, and report on breaking news.
- Key Skills:
- Strong research and investigative skills
- Proficiency in online searching, data verification, and fact-checking
- Familiarity with using OSINT tools for digital investigations
- Industries: News outlets, media organizations, independent journalism.
#
Corporate Investigator / Private Investigator
- Role: Corporate and private investigators use OSINT to support corporate security, compliance, or due diligence efforts. They track down information on individuals or organizations, verifying backgrounds or assessing reputational risks.
- Key Skills:
- Strong investigative skills
- Ability to use open-source tools for background checks and research
- Understanding of legal and ethical standards related to investigations
- Industries: Private investigation firms, corporate security, law firms.
#
Social Media Intelligence (SOCMINT) Analyst
- Role: SOCMINT Analysts specialize in analyzing social media platforms to gather OSINT related to public sentiment, security threats, or crisis management. They use social media as a tool to monitor trends, track events, and identify individuals or groups of interest.
- Key Skills:
- Knowledge of social media platforms and how to collect data from them
- Familiarity with sentiment analysis and social media analytics tools
- Understanding of online behavior and digital footprints
- Industries: Marketing agencies, security firms, political organizations, intelligence agencies.
#
Risk and Compliance Analyst
- Role: In this role, professionals use OSINT to assess potential risks to businesses and organizations. They gather information about potential threats—whether they be from competitors, fraud, cyberattacks, or regulatory concerns—to ensure that their organization remains compliant with laws and best practices.
- Key Skills:
- Understanding of risk management and compliance frameworks
- Proficiency in using OSINT tools for business intelligence
- Ability to analyze and interpret complex data
- Industries: Financial services, consulting, legal firms, multinational corporations.
#
Humanitarian and Crisis Response Analyst
- Role: Professionals in this field use OSINT to assist with humanitarian relief efforts by monitoring disaster areas, tracking political unrest, and providing real-time situational awareness. This may involve analyzing social media, satellite imagery, and local news sources to provide actionable intelligence to aid response teams.
- Key Skills:
- Familiarity with crisis management and humanitarian operations
- Ability to process and analyze real-time data from diverse sources
- Understanding of geopolitical dynamics and crisis zones
- Industries: Non-governmental organizations (NGOs), international aid agencies, government, disaster relief organizations.
#
Skills Needed for OSINT Careers:
- Analytical Skills: The ability to assess large volumes of data, identify patterns, and draw meaningful conclusions.
- Technical Proficiency: Knowledge of OSINT tools and platforms (e.g., Maltego, OpenCage, OSINT Framework, etc.).
- Critical Thinking: The ability to question assumptions, spot inconsistencies, and determine the validity of sources.
- Cybersecurity Knowledge: In some roles, understanding of cybersecurity concepts and techniques is essential.
- Attention to Detail: OSINT requires identifying subtle details that might indicate a threat, vulnerability, or opportunity.
- Communication Skills: OSINT professionals must be able to present findings clearly and effectively to stakeholders or clients.
#
OPSEC and OSINT: Key Considerations for Protecting Your Activities
Operational Security (OPSEC) is the practice of safeguarding sensitive information by understanding how adversaries might exploit publicly available data. When it comes to OSINT, maintaining strong OPSEC can significantly reduce the effectiveness of surveillance and eavesdropping by governments, companies, or malicious actors. The goal is to protect your identity, intentions, and actions from being exposed through publicly accessible information.
Here are several key strategies to enhance OPSEC while using OSINT:
#
Reducing the Effectiveness of Eavesdropping
- Limit Public Exposure: The less personal or sensitive information that is shared online, the harder it becomes for adversaries to track your activities or profile you. Be cautious about what you post on social media, websites, and other online platforms.
- Be Mindful of Metadata: Files and photos often contain embedded metadata (e.g., GPS location data, timestamps, and device information). Stripping metadata before sharing files or photos online can prevent adversaries from gaining additional insights into your activities.
- Use Secure Channels: When discussing sensitive matters, prefer encrypted communications (e.g., encrypted emails, messaging apps, or VPNs) over unprotected platforms to ensure the privacy of your messages.
#
Decreasing the Possibility of Retaliation
- Anonymize Your Digital Footprint: The more difficult it is for someone to associate online activity with you, the lower the risk of retaliation. Use pseudonyms or anonymous accounts when interacting with online communities, especially on platforms where personal details may be exposed.
- Avoid Directly Identifiable Content: When possible, avoid uploading content that can be traced back to you, such as photos that reveal personal locations or identifiable features. Be cautious about revealing your routines, travel habits, or other personal details in online posts.
- Use Privacy Tools: Leverage VPNs, proxy servers, or Tor to mask your IP address and online activities. These tools make it harder for third parties, including your internet service provider (ISP) or platform administrators, to track your online actions.
#
Increasing Anonymity of Your Activities
- Anonymize Your Online Presence: Employ tools like virtual private networks (VPNs), anonymizing search engines (e.g., DuckDuckGo), and encrypted communication services (e.g., Signal) to shield your identity while browsing or engaging in online activities.
- Obfuscate Your Location: Use location-spoofing tools or VPNs that route traffic through different countries to prevent adversaries from pinpointing your geographical location.
- Isolate Sensitive Activities: If engaging in potentially risky online activities, consider doing so in isolated environments. Use separate devices or "clean" user profiles that are not linked to your main identity to prevent cross-contamination of sensitive data.
#
Protecting Your Identity from Platforms and ISPs
- Minimize Data Shared with Platforms: Be cautious about granting too much personal information to online platforms, websites, or services. Review privacy settings to restrict the amount of identifiable information others can access.
- Avoid Overuse of Personal Identifiers: Refrain from using your real name, email address, or phone number when unnecessary. Whenever possible, use disposable or anonymous accounts to access online services.
- Limit Data Sharing with Internet Service Providers (ISPs): Use encrypted connections (SSL/TLS), avoid unsecured networks (e.g., public Wi-Fi), and opt for privacy-focused ISPs that minimize data retention and do not track user activity.
#
Isolating Malicious Links and Documents
- Be Cautious with Links: When working with OSINT or conducting research, always verify the source of any links you click or documents you download. Malicious links or documents can be used to infect your device with malware, track your online movements, or extract sensitive data from your system.
- Use Sandbox Environments: Open suspicious links or attachments in isolated or virtualized environments (i.e., sandboxes) where they cannot interact with your main operating system or data. This practice reduces the risk of malware infection or data exfiltration.
- Verify URLs and Sources: Before clicking on any links, always ensure the URL is legitimate and corresponds to the site you intend to visit. Fake websites often look similar to trusted ones but are designed to steal information or track your activities.
#
Risk Model in OSINT and Privacy Protection
When engaging in Open-Source Intelligence (OSINT) or conducting activities online, it's important to evaluate the risks to your privacy and security. Understanding the potential threats and who or what you need to protect yourself from can help you implement the appropriate security measures. Here’s a breakdown of who or what you might be trying to hide your activity from, along with a guide to the different levels of privacy and protection that may be needed based on the risks you face.
#
Who Are You Trying to Hide Your Activity From?
Your Target
- Risk: If you're conducting OSINT to monitor or investigate a specific individual, organization, or group, the target could potentially identify or retaliate against you.
- Protection Goal: High Anonymity – You need to ensure your identity, methods, and sources of information remain undetected by your target. This can involve using anonymous accounts, obfuscating your location, and minimizing digital footprints.
Web Server Administrator
- Risk: The administrator of the web server you're interacting with may have access to logs that could expose your IP address, login information, or other identifying details.
- Protection Goal: Moderate to High Anonymity – Use of VPNs or proxies can mask your real IP address and prevent the server administrator from identifying your true location or identity.
Internet Service Provider (ISP)
- Risk: Your ISP can see and log your internet traffic, potentially exposing your online activities, including websites visited, services used, and communications. In some cases, they may share this data with third parties or governments.
- Protection Goal: High Privacy – To hide your online activity from your ISP, use tools such as VPNs or Tor that encrypt and anonymize your traffic. This prevents the ISP from seeing the content of your communications and browsing history.
Internet Trackers and Advertisers
- Risk: Advertisers and trackers collect data on your browsing habits, interests, and online behavior to build a profile for targeted advertising. These entities often track users across websites without their consent.
- Protection Goal: Moderate Privacy – Using privacy-focused browsers (e.g., Brave, Firefox with privacy extensions), ad-blockers, anti-tracking tools, and VPNs can reduce your exposure to online tracking and profiling.
Governments
- Risk: Governments, particularly those with sophisticated surveillance capabilities, may monitor your online activities, especially if you're involved in sensitive or high-risk activities (e.g., political activism, investigative journalism, or OSINT for intelligence purposes).
- Protection Goal: High Security and Anonymity – To protect against government surveillance, you should employ tools that ensure strong encryption, end-to-end encrypted communication (e.g., Signal, ProtonMail), anonymous browsing (e.g., Tor), and strong data protection protocols (e.g., encrypted file storage).
#
Risk Protection Model: A Scale of Privacy & Security
#
Protection Spectrum
About You (Identity Protection)
- Low Protection (Basic): If you're only trying to prevent advertisers from tracking your interests, basic tools like ad-blockers or private browsing modes may suffice.
- Moderate Protection (Personal Identity Protection): To avoid being tracked by advertisers or web administrators, use a VPN, anonymous browsing tools, and private social media accounts.
- High Protection (Advanced Anonymity): To protect your identity and avoid being tracked by ISPs or governments, use Tor, encrypted messaging platforms, and strong privacy practices across all platforms.
About Your Network/Computer (Technical Protection)
- Low Protection (Basic): Secure your computer with antivirus software, ensure your Wi-Fi is password-protected, and use HTTPS when browsing websites.
- Moderate Protection (Secure Network): Use a VPN to anonymize your network traffic, employ firewalls, and utilize encrypted communication protocols.
- High Protection (Advanced Security): Use advanced encryption techniques for both data at rest and in transit, configure secure network protocols, and ensure your operating system is hardened against exploits.
Who You Work For (Professional Privacy)
- Low Protection: In a work environment, standard workplace security practices may be enough, but this can depend on the sensitivity of your work.
- Moderate Protection: When handling sensitive company data, ensure all communication is encrypted and access is restricted to authorized personnel.
- High Protection: For those working with highly sensitive or confidential information (e.g., government contractors, journalists), anonymizing tools like Tor, VPNs, and encrypted communication should be used to safeguard against corporate espionage or government surveillance.
What You Are Doing (Operational Security)
- Low Protection: If you’re engaging in basic research or publicly accessible activities, standard security measures are generally sufficient.
- Moderate Protection: For more sensitive activities (e.g., investigative work, competitive intelligence), extra steps should be taken to protect your identity and methods (VPNs, encrypted communications).
- High Protection: For high-risk operations (e.g., OSINT on criminal groups, whistleblowing, political activism), every detail must be encrypted, anonymized, and secured to prevent exposure or retaliation. This includes using Tor, encrypted messaging apps, secure email services, and advanced OPSEC measures.
#
Intelligence Lifecycle
The OSINT process follows the broader Intelligence Lifecycle, which consists of several key stages:
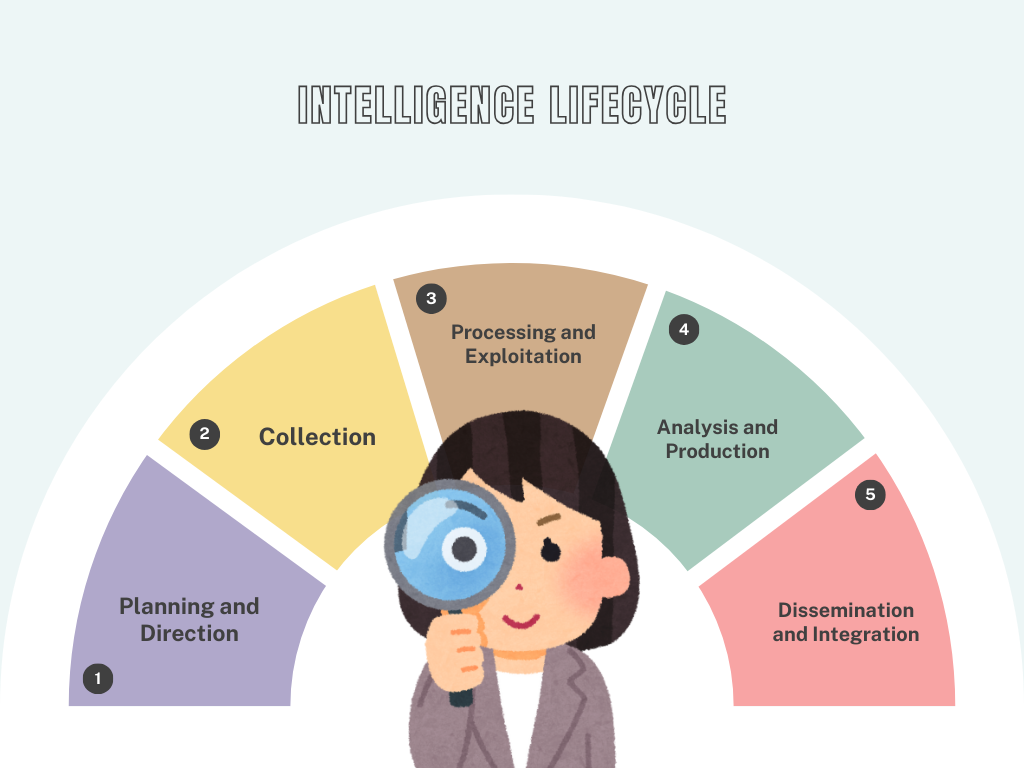
Planning and Direction:
- Defining the intelligence requirements and setting objectives.
- Guiding the overall direction of the intelligence efforts.
Collection:
- Gathering relevant data from public sources such as social media, news outlets, public databases, websites, etc.
Processing and Exploitation:
- Transforming collected data into a usable format, including translation, categorization, and other forms of processing.
Analysis and Production:
- Analyzing processed data to extract actionable insights, identify patterns, and draw conclusions.
Dissemination and Integration:
- Sharing the intelligence with appropriate stakeholders.
- Ensuring the intelligence is integrated into decision-making processes.
#
Note-Taking in OSINT
Effective note-taking is crucial throughout the OSINT process. It involves documenting sources, analyses, and decisions to ensure transparency, accountability, and the ability to review and verify the gathered intelligence.
#
Recommended Note-Taking Apps & Tools
- KeepNote: An older, reliable note-taking app.
- Notion: A modern, flexible tool with extensive features.
- CherryTree: A hierarchical note-taking application.
- Obsidian: A highly customizable and private note-taking app.
- GreenShot: A robust screenshot tool.
- Flameshot: A Linux alternative for screenshot capturing.
#
Introduction to Sock Puppets
A Sock Puppet in OSINT (Open-Source Intelligence) refers to a fake online identity created to deceive or manipulate others. These identities are often used in intelligence operations to gather information, influence opinions, or infiltrate groups without revealing the operator's true identity or intentions. Creating and managing sock puppets effectively requires careful planning and adherence to ethical and legal standards.
#
The Art of the Sock
Sock puppets are where OSINT intersects with HUMINT (Human Intelligence). Social media is saturated with sock puppets influencing conversations across various platforms. They are employed by nation-states for political influence, by corporations to sway brand perception, or by malicious actors to deceive and defraud. OSINT investigators also use sock puppets, creating clean, credible personas to engage their targets.
#
OSINT and HUMINT: A Combined Approach
OSINT isn’t just about gathering publicly available information. It often requires blending with HUMINT, especially in investigations where public signals are limited. To truly understand a target, you may need to engage them directly through social engineering, which involves interacting with targets under the guise of a sock puppet.
#
Beware of Sock Hunters
While creating and using sock puppets, it’s important to understand how they can be detected. Sock puppets can often be identified by their writing style, posting activity, and relationships with other users. Tools and algorithms can analyze these patterns to unmask sock puppets, especially if the operator is careless with their operational security (OPSEC).
Machine learning tools can identify similarities in behavior across multiple social accounts, creating a "behavioral fingerprint" that can reveal sock puppet operators, even if they attempt to randomize their actions. These detection tools are increasingly used in countering information warfare and disrupting malicious online activities.
#
The Sock Puppet Lifecycle
#
What is a Sock Puppet?
A sock puppet is a fully fleshed-out social persona with a credible history across different platforms. A well-maintained sock puppet behaves like a real person online, with consistent activity that spans various social networks like LinkedIn, Facebook, and Twitter.
#
Think Long Term
Creating a convincing sock puppet requires a long-term strategy. Freshly created social media accounts are easily spotted as fake, so it’s crucial to develop a sock puppet well before it’s needed. This involves creating a credible social history, engaging in authentic activities, and avoiding interaction with your real identity or other sock puppets.
#
The Importance of a Credible History
A sock puppet’s credibility is based on a breadcrumb trail of activity that mirrors a real person's online behavior. This includes regular interactions on social media, a LinkedIn profile with a plausible work history, and a Facebook profile with personal photos and posts. The more extensive the social history, the more convincing the sock puppet becomes.
#
Leveraging Gender in Sock Puppetry
Male users are often more susceptible to social engineering by female personas, making it advantageous to create female sock puppets when targeting men. However, it’s important to remain cautious, as sophisticated targets may be wary of direct approaches from attractive women online.
#
Softly Softly Catchee Monkey
Deception is most effective when the target believes in the authenticity of the sock puppet. This involves building a unique, consistent personality for the sock puppet and engaging in activities that make the puppet noticeable to the target before direct interaction occurs. This strategy, often referred to as “softly, softly, catchee monkey,” emphasizes patience and subtlety in OSINT operations.
#
Creating an Effective Sock Puppet for OSINT Investigations
#
Introduction and Philosophy
Creating a successful sock puppet involves a clear understanding of your intent. Whether you’re creating a fully fleshed-out persona or an avatar focused on a specific idea, the goal is to build trust and credibility online. The success of a sock puppet depends on its ability to interact authentically and convincingly within its intended social environment.
#
The Setup
Creating a sock puppet requires several key tools and practices to ensure anonymity and credibility:
- Dedicated Computer: Use a dedicated device for sock puppet activities to avoid linking them to your real identity.
- Encrypted Email: Use encrypted email services like ProtonMail to protect your communications.
- Phone Number: Obtain a dedicated phone number, preferably through a burner phone or a service like Google Voice.
- VPN: Mask your IP address using a VPNs Like Proton, Nord Vpn, etc to prevent your activities from being traced back to you.
- Social Media Profiles: Create social media profiles that align with your target’s interests and engage authentically over time.
- Virtual Machines: Use virtual machines for additional layers of privacy and to compartmentalize different sock puppet activities.
By carefully setting up and maintaining a sock puppet, you can create a convincing online persona that can be used for effective OSINT investigations while minimizing the risk of exposure. Now, this is just a start, but it will help you at least get started. You will have to customize your avatar as you go along to maintain or add credibility.
#
Blog Creation for Your Avatar
To give your sock puppet more depth and credibility, consider creating a blog on platforms like WordPress, Medium, or Blogger. This blog should be linked to your sock puppet’s social media profile, providing a consistent and authentic online presence. Regularly update your blog with content that aligns with the persona you've created on social media. This will not only increase your avatar's credibility but also help in creating a complex and believable character over time.
#
Chrome Extensions for Enhanced Anonymity
Staying anonymous online requires blocking tracking mechanisms that can reveal your identity. Two essential Chrome extensions for this purpose are AdBlock and Disconnect Me. AdBlock will prevent ads from tracking you, while Disconnect Me blocks social media sites from tracking your online activities. When used together with a VPN, these tools provide a robust layer of protection for anonymous browsing.
#
Bonus Tip: Verifying Your Identity on Keybase
Once your sock puppet is fully developed, you might want to take the next step by verifying your identity on Keybase. This platform allows you to secure your identity and open dialogues within Slack channels, Rocket Chats, or other communication platforms. It’s a great way to engage with your target or associates in a more controlled and secure environment outside of mainstream social media.
#
Things to Consider Before Deploying Your Sock Puppet
Before you start using your sock puppet, it's crucial to take the time to fully develop it. Deploying it too early can result in a loss of credibility that may be difficult to recover from. Set specific goals, such as a certain number of tweets, followers, or blog posts, before using your sock puppet for its intended purpose. Allow your sock puppet to grow organically and naturally steer its direction based on the influence it garners. This organic growth is why it's also advisable to have multiple sock puppet accounts.
Another critical aspect to consider is forensic linguistics. The content created by your sock puppet should be distinct from your personal account. Although you’re unlikely to draw suspicion if you’re not engaging in highly controversial activities, it’s still wise to collect OSINT on your sock puppet and analyze it as though you were an outsider. Ask a friend or colleague to review your sock puppet and identify any potential weaknesses before deployment.
#
Common Pitfalls to Avoid
Some common mistakes made by those creating sock puppets include using easily traceable stock images, neglecting Whois protection during domain registration, deploying their socks too soon, and failing to conduct OSINT or self-investigation before deployment. For more insights, check out Aric Toler’s analysis of these pitfalls.
#
Setting Up an Anonymous Sock Puppet Account
This process outlines the steps to create an anonymous sock puppet account for OSINT or other investigative purposes. It’s designed to minimize risks and maintain operational security (OPSEC). Here's a summary of the key points:
#
1. Persona Creation
- Objective: Define the identity and purpose of your sock puppet.
- Tool: Use Fake Name Generator to create a realistic identity.
- Tip: Ensure the persona fits the narrative you want to establish.
#
2. Visual Identity
- Objective: Create a believable image for your sock puppet.
- Tool: Use This Person Does Not Exist to generate a unique image.
- Reverse Image Search: Verify uniqueness of generated images.
- Tip: Inspect and edit the image to fix any flaws, using tools like Photoshop, GIMP, or Affinity Photo.
#
3. Secure Communication
- Objective: Obtain a burner phone and secure communication channels.
- Tools:
- Burner phone: A wiped, fresh device compatible with Mint Mobile.
- Burner credit card: Use Privacy.com for online purchases.
- Tip: Ensure no links to your real identity by purchasing SIM cards and credit services anonymously.
#
4. Account Setup
- Objective: Establish online accounts for your sock puppet.
- Steps:
- Set up a burner Amazon account for purchasing SIM cards.
- Buy Mint Mobile SIM cards, preferably through an anonymous Amazon order.
- Use a VPN to mask your location, set to the area where your sock puppet is "located."
- Register accounts (Google, ProtonMail, etc.) using the Mint Mobile trial number.
- Set up Two-Factor Authentication (2FA) on all accounts.
#
5. Finalization
- Objective: Secure and finalize the sock puppet’s online presence.
- Steps:
- After setting up 2FA, switch to a more permanent, secure phone number (like MySudo or Google Voice).
- Verify that everything works as intended.
- Destroy the Mint Mobile SIM card.
- Wipe the burner phone to remove any traceable data.
#
Key Considerations:
- Anonymity: All actions should be conducted with the highest regard for privacy and anonymity.
- OPSEC: Maintain strict operational security to prevent any link to your real identity.
- Realism: The sock puppet must be believable, with consistent online behavior matching the persona.
By following these steps, you'll create a robust and credible sock puppet that can withstand scrutiny and serve its intended purpose effectively.
#
Search Engines for OSINT
When conducting Open Source Intelligence (OSINT), using a variety of search engines can yield more comprehensive results. Different search engines have unique strengths and regional focuses, making them valuable tools in an investigator's toolkit. Here’s a brief overview of key search engines used in OSINT:
This table provides a quick overview of each search engine's strengths and weaknesses in the context of OSINT investigations. By selecting the appropriate search engine and applying advanced operators, OSINT practitioners can uncover a wealth of valuable information while maintaining privacy and efficiency.
#
Search Engine Operators
Search engine operators are specific commands or symbols that help refine search results, making it easier to find precise information on the internet. These operators are essential tools in OSINT (Open-Source Intelligence) investigations, allowing investigators to narrow down search results, find specific files, and uncover hidden information.
#
Basic Search Operators
Quotation Marks (""):
- Purpose: To search for an exact phrase or sequence of words.
- Example:
"social engineering tactics"
Minus Sign (-):
- Purpose: To exclude certain words from the search results.
- Example:
cybersecurity -hacking
OR Operator:
- Purpose: To search for pages containing at least one of the specified terms.
- Example:
data breach OR data leak
Wildcard (*):
- Purpose: To substitute any unknown terms or words in a search query.
- Example:
"how to * a VPN"
Site: Operator:
- Purpose: To restrict searches to a specific website or domain.
- Example:
site:gov "cybersecurity guidelines"
Filetype: Operator:
- Purpose: To search for specific file types (e.g., PDFs, DOCs).
- Example:
filetype:pdf "phishing prevention"
Inurl: Operator:
- Purpose: To search for URLs containing specific words or phrases.
- Example:
inurl:login
Intitle: Operator:
- Purpose: To search for pages with specific words in the title.
- Example:
intitle:"OSINT tools"
Related: Operator:
- Purpose: To find websites related to a specified site.
- Example:
related:nytimes.com
Cache: Operator:
- Purpose: To view a cached version of a webpage.
- Example:
cache:example.com
#
Advanced Search Techniques
Combining Operators:
- You can combine multiple operators to refine your search further.
- Example:
site:edu "cybersecurity policy" filetype:pdf
Using Parentheses for Grouping:
- Parentheses can group terms and operators to control the order of operations in complex searches.
- Example:
(intitle:report OR intitle:analysis) AND "2023"
Intext: Operator:
- Purpose: To find pages where the specified term appears in the body text.
- Example:
intext:"data exfiltration"
Allinurl: and Allintitle: Operators:
- Purpose: To search for pages where all specified words appear in the URL or title.
- Example:
allinurl:login passwordorallintitle:"OSINT" guide
AROUND(X) Operator:
- Purpose: To find pages where two words are within a certain distance of each other.
- Example:
cybersecurity AROUND(3) training
#
Practical Applications in OSINT
Finding Specific Documents:
- Example:
site:gov filetype:pdf "cybersecurity report"can be used to locate government cybersecurity reports in PDF format.
- Example:
Locating Exposed Information:
- Example:
inurl:"admin" filetype:txtmight reveal text files containing admin login details.
- Example:
Narrowing Down Sources:
- Example:
site:reddit.com "OSINT tools"can be used to find discussions about OSINT tools specifically on Reddit.
- Example:
Search engine operators are powerful tools that enhance your ability to find relevant information quickly and efficiently. Mastering these operators is crucial for anyone involved in OSINT investigations, enabling them to uncover critical data that might otherwise remain hidden. By combining these operators, you can perform highly targeted searches, making your investigative efforts more effective.
#
Reverse Image Search
Reverse Image Search is a method that allows users to find information about an image by searching the internet for similar or identical images. Instead of using text-based queries, users can upload an image or provide an image URL, and the search engine scans its database for matches. This technology is useful for various purposes, from identifying unknown objects to verifying the authenticity of an image.
#
Uses of Reverse Image Search
- Identify Unknown Objects or Locations: Helps recognize landmarks, objects, or locations within an image.
- Find the Source of an Image: Allows users to trace an image back to its original source, useful for authenticity verification.
- Detect Copyright Infringements: Enables photographers and content creators to find unauthorized uses of their images online.
- Fact-Check: Journalists and researchers can verify the context of an image to prevent misinformation.
- Locate Products: Shoppers can find visually similar products or compare items available for purchase online.
- Person Search: Helps in identifying individuals or tracking their online presence through their images.
#
Perform a Reverse Image Search
#
Using Google Images
- Upload an image from your device or paste an image URL.
- Google will display visually similar images and websites where the image appears.
#
Using TinEye
- A specialized reverse image search engine.
- Upload an image or enter the image URL.
- TinEye shows where the image has appeared online, sorted by date and relevance.
#
Using Bing Visual Search
- Upload an image or paste a URL.
- Bing provides similar images and related content.
#
Using Yandex Images
- Particularly strong in finding images from Russian-language websites and may produce different results than Google.
#
Using GeoSpy AI
- A tool that predicts the location of a photo using AI technology, adding an extra layer of analysis to image searches.
#
Mobile Reverse Image Search
On mobile devices, reverse image search can be performed through:
- Google Lens: Available within the Google Photos app or as a standalone app, allowing users to perform reverse image searches directly from their mobile devices.
- Browser Workaround: In mobile browsers like Chrome, long-press an image and select "Search Google for this image."
#
Considerations
- Privacy: Be cautious when uploading sensitive images, as they may be stored or indexed by search engines.
- Accuracy: Results can vary across different services, so it's often beneficial to try multiple reverse image search engines.
#
Exif Data
Exif Data (Exchangeable Image File Format) is metadata embedded within digital photos that provides detailed information about the image's attributes. This data, embedded automatically when an image is taken, includes a wealth of information, such as camera settings, timestamps, and even GPS coordinates. While useful in various professional fields, Exif data also presents privacy concerns as it may unintentionally reveal sensitive details.
#
Key Components of Exif Data
- Camera Information: Includes details like the camera model, lens type, and sometimes the serial number.
- Date and Time: Records the precise date and time the image was captured.
- Location Data: GPS coordinates showing where the image was taken, if the camera or smartphone had location services enabled.
- Camera Settings: Technical details such as aperture, shutter speed, ISO, and focal length.
- Software Information: Data about the software used to edit or process the image, if applicable.
#
Applications of Exif Data
#
Photography
- Skill Improvement: Photographers review Exif data to analyze the settings used in their best shots, helping them refine their technique.
#
Forensic Analysis
- Authenticity Verification: Investigators use Exif data to verify the origin of an image, identify any alterations, and understand the context of how and when it was taken.
#
Geolocation
- Location Verification: By extracting GPS coordinates from Exif data, one can pinpoint the location of an image's capture, which is useful in many investigations.
#
Chronological Context
- Event Timeline Construction: Exif data helps in verifying the date and time of an image, which can be critical in legal investigations or media fact-checking.
#
Image Editing Tracking
- Processing History: Exif data allows for tracking the software and steps involved in editing an image, which is essential in detecting manipulations or deepfakes.
#
Role of Exif Data in OSINT Investigations
Exif Data is particularly valuable in OSINT (Open Source Intelligence) investigations due to its ability to reveal hidden or overlooked details in digital images. Here’s how it plays a crucial role:
#
Location Tracking (Geolocation)
- GPS Coordinates: Exif data often contains GPS information that can pinpoint the precise location where a photo was taken, aiding in the tracking of individuals or verifying locations in conflict zones.
#
Date and Time Verification
- Timeline Accuracy: The embedded date and time can be cross-referenced with other information sources to verify or debunk claims related to when an image was captured.
#
Camera and Device Information
- Identifying Patterns: Camera model and settings can sometimes be linked to specific users or groups, allowing investigators to establish connections between images.
#
Authenticity Checks
- Detecting Manipulations: Exif data can reveal if an image has been edited or altered, indicating potential tampering or the use of editing software.
#
Device Tracing
- Identifying Devices: Information such as the device model and serial number embedded in Exif data can be used to trace back to the owner or user of the device.
#
Pattern Recognition
- Cross-Image Analysis: Repeated analysis of Exif data across multiple images can help uncover patterns such as recurring locations, camera settings, or times, providing valuable insights.
#
Tools for Extracting and Analyzing Exif Data
To effectively utilize Exif data in OSINT, several tools can extract and analyze this metadata:
- ExifTool: A versatile command-line tool for extracting and editing Exif metadata.
- Jeffrey’s Exif Viewer: An online tool for easy extraction and viewing of Exif data.
- Fotoforensics: A tool that not only extracts Exif data but also helps identify image manipulations.
- ExifCleaner: This tool can remove Exif data from images to protect privacy before sharing.
#
Limitations of Exif Data
- Data Manipulation: Exif data can be edited or removed, so it's essential to corroborate findings with additional evidence.
- Social Media Platforms: Many platforms strip Exif data from images to protect user privacy, reducing the effectiveness of Exif analysis.
- Image Compression: Repeated editing or compression of an image may degrade or erase Exif data, making it difficult to retrieve useful information.
Exif data is a powerful tool for photographers, investigators, and OSINT professionals. However, its usefulness is tempered by potential privacy concerns and the limitations posed by data manipulation and removal. Properly leveraging Exif data requires understanding its strengths and weaknesses and using appropriate tools to extract and analyze it effectively.
#
Viewing Exif Data
#
ExifTool (Command-Line)
ExifTool is a powerful command-line tool that can be used to view Exif data from images.
Command:
exiftool image.jpg- Explanation: This command will display all the Exif metadata embedded in the
image.jpgfile.
#
Windows File Explorer
You can view basic Exif data directly from Windows File Explorer.
Steps:
- Right-click the image file.
- Select Properties.
- Go to the Details tab to view the Exif data.
#
macOS Preview
On macOS, you can use the Preview app to view Exif data.
Steps:
- Open the image in Preview.
- Go to Tools > Show Inspector.
- Click on the i (information) icon to view the metadata.
#
Online Tools (Jeffrey’s Exif Viewer)
You can also use online tools to view Exif data without installing software.
Steps:
- Visit Jeffrey’s Exif Viewer.
- Upload your image or provide a URL to the image.
- View the displayed Exif data.
#
Removing Exif Data
#
ExifTool (Command-Line)
ExifTool can also be used to remove Exif data from images.
Command:
exiftool -all= image.jpg- Explanation: This command will strip all Exif metadata from
image.jpg. The original file is saved asimage.jpg_original, and the cleaned file retains the original name.
#
Windows File Explorer
Windows provides a simple way to remove Exif data from images.
Steps:
- Right-click the image file.
- Select Properties.
- Go to the Details tab.
- Click on Remove Properties and Personal Information.
- Choose Create a copy with all possible properties removed or Remove the following properties from this file, then click OK.
#
macOS Preview
You can use Preview on macOS to remove Exif data, though it is a bit indirect.
Steps:
- Open the image in Preview.
- Export the image using File > Export.
- In the export dialog, uncheck the Include Metadata option before saving the file.
#
ExifCleaner (Software)
ExifCleaner is a dedicated tool for stripping Exif data from images.
Steps:
- Download and install ExifCleaner.
- Drag and drop the images into the tool.
- The Exif data is automatically removed, and you can download the cleaned images.
#
Physical Location OSINT
Physical Location OSINT (Open Source Intelligence) is a powerful method used to determine or verify physical locations by leveraging publicly available data. It plays a significant role in various fields, including journalism, law enforcement, intelligence, and disaster response. This blog post dives into the techniques and tools used in Physical Location OSINT, offering an overview of how geolocation is achieved and what challenges analysts face when working with open-source data.
#
Techniques for Identifying Geographical Locations
Visual Clues in Images and Videos
- Landmarks and Terrain: Landmarks, recognizable buildings, monuments, or natural features like mountains, rivers, or vegetation often provide essential clues to determine a location. For example, an iconic building in the background of a video can help identify where it was filmed. Terrain analysis—such as looking at hills, plains, or coastal features—can also narrow down possible locations.
- Signage and Language: Analyzing the language on street signs, billboards, and storefronts helps pinpoint regions or countries. A street sign in Cyrillic suggests a location in Eastern Europe or Central Asia, while Arabic script indicates the Middle East or North Africa.
- Vehicle Types and License Plates: The style of vehicles, specific regional models, or license plate designs can also help narrow down the country or region. For instance, analyzing the colors, fonts, or configurations of license plates can help identify the location where the media was captured.
Metadata Extraction
- EXIF Data: EXIF (Exchangeable Image File Format) data embedded in images often includes metadata such as GPS coordinates, timestamps, and device information. If the GPS data is present, it can provide the exact latitude and longitude where the image was taken. Metadata extraction tools like ExifTool allow investigators to extract and analyze these details, aiding in location verification.
- Tool Example: Another useful tool is Jeffrey's Exif Viewer, which provides an easy-to-use interface to upload and extract metadata from images.
Reverse Image Search
- Google Reverse Image Search: This method helps identify the location of an image by finding visually similar images online. If the image has been previously uploaded to another site with location information, it can provide additional clues. The search tool is available at Google Images.
- TinEye: Similar to Google’s tool, TinEye allows users to upload an image and search for it across the web. This can help find other instances of the image and provide insights into its origin or location.
Shadow Analysis
- Sun Position and Shadows: Sun position and shadow length in an image or video can help determine the time of day and geographical latitude. By analyzing the angle of shadows, an investigator can infer the approximate location and time. SunCalc is a tool that allows users to calculate sun position based on the time and location of the photograph or video, helping determine more details about where and when the image was taken.
Cross-Referencing with Maps
- Google Earth/Maps: These tools are commonly used in OSINT investigations. By using Google Maps and its Street View feature, investigators can compare the visual elements in an image to known locations. Google Earth provides more detailed satellite imagery and 3D terrain views, which can assist in geospatial analysis.
- ArcGIS: For more advanced geospatial analysis, ArcGIS is an industry-standard tool. It allows for mapping, analyzing, and visualizing geographic data to help confirm the location of events, objects, or individuals.
Social Media Geolocation
- Geotagged Posts: Social media platforms are rich sources of location data. Many posts are geotagged, meaning they include GPS data indicating where they were posted. Twitter’s Advanced Search and Instagram’s location search features allow investigators to find posts tagged with specific places, helping to trace events or movements.
- YouTube Geotagging: Video content uploaded to platforms like YouTube can also be geotagged. By analyzing the metadata attached to videos, investigators can track where the content was filmed.
Crowdsourced and Collaborative Mapping Tools
- OpenStreetMap: OpenStreetMap is a user-generated map of the world that includes detailed information about roads, buildings, and landmarks. It is widely used in OSINT investigations to gather localized data. Access it at OpenStreetMap.
- Wikimapia: Combining satellite imagery with user-contributed information, Wikimapia is another valuable tool for gathering data about specific locations. This platform often contains user-provided details about landmarks and geographical features.
Language and Cultural Markers
- Text and Language Analysis: Analyzing the language used in media, whether on signs, documents, or spoken in videos, can provide vital location information. By identifying the language or dialect, investigators can narrow down potential countries or regions.
- Cultural Indicators: Local customs, clothing, and symbols can be cultural markers that hint at a specific location. For example, the style of architecture or even regional clothing can indicate a country or city.
#
Key Tools for Physical Location OSINT
Google Earth/Maps: Offers satellite imagery and 3D terrain analysis to explore locations worldwide. Google Earth and Google Maps are essential tools for identifying geographical features and verifying location clues.
ArcGIS: A robust tool for mapping, geospatial analysis, and data visualization. Analysts can map out locations and analyze spatial relationships. Find it at ArcGIS.
Sentinel Hub: Provides high-resolution satellite imagery, often used for monitoring large areas. This tool is ideal for analyzing geographical changes over time or during crises. Visit Sentinel Hub.
Mapillary: A service that collects street-level imagery, often crowdsourced, providing a searchable database of real-world photos. It is useful for confirming visual elements in a specific location. Explore more at Mapillary.
What3words: This tool divides the world into 3m x 3m squares, each with a unique identifier made of three words. It’s excellent for pinpointing exact locations. Learn more at What3words.
SunCalc: Use this tool for shadow analysis, which helps estimate the time and location of an image based on the sun's position. Check it out at SunCalc.
#
Practical Applications of Physical Location OSINT
Crisis Response and Disaster Relief
- Disaster Relief: In the aftermath of hurricanes, earthquakes, or other natural disasters, OSINT analysts use geotagged social media posts, satellite imagery, and street view data to locate survivors and assess damage. Tools like Sentinel Hub and Google Earth are particularly useful for tracking the impact on infrastructure and organizing relief efforts.
- Evacuation Planning: During crises, real-time location data helps plan safe evacuation routes and locate shelters. Social media platforms and geotagged posts often provide the most up-to-date on-the-ground reports.
Investigative Journalism
- Verifying Locations: Journalists use OSINT techniques to verify locations where important events occurred. For instance, analyzing satellite images or reverse searching images shared online can help confirm the authenticity of a claim.
- Tracking Movements: Social media geolocation and metadata analysis are powerful tools for tracking the movements of individuals or groups. This has been crucial in conflicts and crises, such as monitoring refugee flows or troop movements during armed conflicts.
Law Enforcement and Intelligence
- Suspect Tracking: By analyzing location data from social media posts, law enforcement agencies can trace suspects' movements or locate missing persons. Tools like ExifTool for metadata extraction and geotagged social media posts are often employed.
- Border Security: OSINT can assist in monitoring border regions for illegal activities. Analysts use satellite imagery, social media posts, and mapping tools like ArcGIS and Sentinel Hub to identify unauthorized crossings.
Military and Defense
- Reconnaissance: Analyzing satellite imagery and geospatial data helps military personnel identify strategic locations, monitor troop movements, or assess damage to infrastructure. Tools like Sentinel Hub and Google Earth are often used for reconnaissance and intelligence gathering.
- Operational Planning: By analyzing real-time location data, defense operations can be planned and executed with greater precision. Geospatial tools like ArcGIS provide detailed maps that support decision-making in complex environments.
#
Challenges and Considerations
- Data Accuracy: Not all geolocation data is accurate. Some data, especially on social media, can be intentionally falsified. Therefore, verifying location information through cross-referencing is a critical step in any investigation.
- Privacy Concerns: Extracting and analyzing location data, especially from private individuals,
raises ethical and legal questions. It is crucial to balance intelligence gathering with respect for privacy and applicable laws.
- Information Overload: With the vast amount of data available online, analysts can face the challenge of sifting through irrelevant or misleading information. OSINT investigations require rigorous filtering to extract actionable insights.
Physical Location OSINT involves a combination of image analysis, metadata extraction, geospatial tools, and social media monitoring to uncover geographical locations. With the help of tools like Google Earth, ExifTool, ArcGIS, and others, investigators can accurately identify and verify locations. Whether applied in disaster response, journalism, or intelligence, these techniques and tools are crucial for turning open-source data into actionable intelligence.
#
Case Studies
MH17 Investigation
- Investigative journalists and OSINT professionals used satellite imagery, social media posts, and geotagged photos to track the movement of the missile launcher used in the downing of Malaysia Airlines Flight MH17. By cross-referencing these data points, they were able to establish a timeline and identify the location of the launcher at key moments.
Tracking Armed Conflicts
- During conflicts such as those in Syria and Ukraine, OSINT analysts have used geotagged images, satellite imagery, and social media reports to map out conflict zones, monitor troop movements, and verify the locations of attacks. This data has been used to corroborate or refute claims made by the parties involved.
Natural Disaster Response
- In the aftermath of events like hurricanes or earthquakes, OSINT professionals use social media monitoring, geotagged content, and satellite imagery to locate survivors, assess damage, and coordinate relief efforts. These techniques have proven vital in quickly identifying areas most in need of assistance.
#
Email OSINT - Discovering Email Addresses
Email OSINT (Open Source Intelligence) refers to the practice of gathering email addresses using publicly available resources. This method is essential in various fields, including cybersecurity, investigative journalism, digital marketing, and competitive intelligence. Below is a detailed guide on the techniques, tools, and ethical considerations involved in discovering email addresses.
#
Techniques for Discovering Email Addresses
#
Search Engines
Search engines like Google and Bing are powerful tools for discovering email addresses, especially when used with advanced search operators.
Google Search:
- Basic Search: Start with simple queries such as
"John Doe email","contact John Doe", or"John Doe @gmail.com". - Advanced Operators:
site:domain.com email- This query restricts the search to a specific domain, useful for targeting a company's website."contact us" email- This search looks for pages that likely contain email addresses, such as contact or about pages.filetype:pdf "John Doe"- Searches for PDFs that might list contact information, useful for academic papers or corporate reports.intitle:"index of" "email"- Searches for directory listings or indexes that might contain email addresses.
- Basic Search: Start with simple queries such as
Bing Search:
- Bing's search capabilities are similar to Google, but its algorithm may yield different results. Use queries like:
site:domain.com "email"- A domain-restricted search to find email addresses on a specific website.inurl:contact "John Doe"- This search might uncover pages with email addresses embedded in URLs.
- Bing's search capabilities are similar to Google, but its algorithm may yield different results. Use queries like:
#
Social Media Platforms
Social media platforms are rich sources of personal and professional information, often including email addresses.
-
- Profile Review: Many professionals list their email addresses on their LinkedIn profiles, especially in the contact information section.
- Advanced Search: LinkedIn’s search features allow you to filter results by company, location, industry, and more, making it easier to find specific individuals or groups.
- LinkedIn Plugins: Tools like LinkedIn Sales Navigator can be used to export email addresses, though these are typically paid services.
-
- Bio Scrutiny: Some users include their email addresses in their bios. Searching for
"email"or"contact"within a user's profile can be effective. - Tweet Search: Use Twitter’s advanced search to find tweets containing
"email"or"contact me", followed by relevant keywords related to your target. - Advanced Operators: Combine search operators like
from:username "email"to search for email mentions by specific users.
- Bio Scrutiny: Some users include their email addresses in their bios. Searching for
-
- Profile Information: Users sometimes list email addresses on their profiles, particularly in the "About" section.
- Group Searches: Email addresses can sometimes be found in posts within specific groups or in page posts by businesses.
#
Email Lookup Services
These specialized services are designed to find and verify email addresses using various algorithms and databases.
-
- Domain Search: Enter a company’s domain to find all associated email addresses. Hunter.io’s algorithm identifies common email patterns within the domain.
- Email Finder: Enter a name and company domain to guess an individual’s email address. It also provides a confidence score.
- Verification: Validate the email addresses to check if they are deliverable, helping reduce bounce rates in email campaigns.
-
- Name-Based Search: Similar to Hunter, Voila Norbert allows you to find email addresses by entering a person’s name and domain.
- Bulk Search: Perform bulk searches for multiple email addresses simultaneously, useful for large campaigns.
- Integration: Integrates with CRM systems like Salesforce, allowing seamless data transfer and management.
-
- Gmail/Outlook Integration: Clearbit Connect integrates with Gmail and Outlook, showing relevant information about contacts directly within your inbox.
- Enrichment: Beyond finding email addresses, Clearbit Connect enriches profiles with social media handles, company information, and more.
- Data Accuracy: Clearbit provides highly accurate data, making it ideal for sales and marketing professionals who require precise targeting.
#
Company Websites
Exploring a company’s website can yield useful contact information, particularly on certain pages.
Contact Pages:
- Direct Access: Most companies list general contact email addresses (e.g., info@domain.com, support@domain.com) on their contact pages.
- Role-Specific Emails: Look for email addresses related to specific departments or roles, such as HR, PR, or sales.
- Localized Contacts: Some companies provide email addresses for different regions or branches, useful for targeted outreach.
Staff Directories:
- Team Pages: Many companies have team or staff pages that list email addresses for individual employees. These can be invaluable for personalized outreach.
- Press/Media Pages: Look for press contacts on media pages, which often include direct email addresses for PR representatives.
#
Email Pattern Discovery
Many organizations follow standard email formatting conventions, which can be reverse-engineered to guess email addresses.
Common Patterns:
- First.Last@domain.com
- FirstInitialLast@domain.com
- First@domain.com
- Tools: Tools like Email Permutator+ allow you to generate multiple variations of potential email addresses based on a person's name and company domain.
Pattern Recognition Tools:
- Hunter.io’s Email Finder: Besides generating patterns, it compares them against its database to suggest the most likely correct address.
- Pattern Search via Search Engines: Use search engines to check for common email patterns associated with a particular domain.
#
Data Breaches and Leaks
Sometimes, email addresses become publicly available through data breaches or leaks. While this is a sensitive area, it can provide leads.
-
- Breach Search: Enter an email address to check if it has been compromised in any known data breaches. Useful for verifying the validity of email addresses.
- Domain Search: Check if a specific domain has been exposed in breaches, which can help assess the security posture of an organization.
-
- Breach Database Search: Use Dehashed to search for email addresses in various data breaches. It’s a paid service but offers a comprehensive database.
- Keyword Search: Search for associated usernames, domains, or keywords to find related breaches and exposed email addresses.
#
Public Records and Directories
Certain public records and directories can provide access to email addresses, especially for businesses and professionals.
WHOIS Records:
- Domain Registration: WHOIS databases can reveal the email addresses of domain registrants, often used by domain administrators and owners.
- WHOIS Tools: Use services like WHOIS Lookup to find email addresses linked to domain registrations. Some registrars may hide this data due to GDPR, but it can still be useful in many cases.
Professional Associations:
- Membership Directories: Many professional organizations, such as bar associations, medical boards, or trade organizations, provide directories that include members' contact information.
- Conference Attendee Lists: Sometimes, attendee lists from conferences or webinars are made public, providing a treasure trove of email addresses.
#
Online Forums and Communities
Individuals often share email addresses in public forums, especially in specialized or niche communities.
Specialized Forums:
- Industry-Specific Boards: Explore forums relevant to specific industries or hobbies where users might share their contact details.
- Profile Information: Users often include email addresses in their forum profiles, which can be accessed publicly.
Community Boards:
- Job Boards/Marketplace Sites: Platforms like GitHub, Stack Overflow, or even Craigslist might have users who list email addresses for contact.
- Public Discussions: Scour public discussions for posted email addresses, especially in threads offering services or advice.
#
Web Scraping
Web scraping involves using automated tools to extract data, including email addresses, from websites.
Custom Scripts:
- Scrapy: This Python-based web scraping framework allows you to build spiders that can crawl websites and extract email addresses systematically.
- Beautiful Soup: Another Python library that helps parse HTML and extract data, particularly useful for static websites.
Pre-Built Tools:
- Email Extractors: Tools like Email Extractor or Octoparse can be configured to search websites for email addresses and compile them into a database.
#
Tools for Email Discovery
Features:
- Domain Search: Find all email addresses associated with a specific domain.
- Email Finder: Locate an individual's email address using their name and company.
- Bulk Email Search: Perform searches in bulk, ideal for large campaigns.
- Email Verification: Check if an email address is valid and deliverable.
Use Cases: Perfect for sales teams, recruiters, and marketers who need to build targeted email lists efficiently.
Features:
- Name-Based Email Finder: Input a name and domain to find the correct email address.
- Bulk Search: Conduct bulk searches to gather large lists of email addresses at once.
- CRM Integration: Seamlessly integrate with CRM tools for better data management.
- Email Verification: Ensure the validity of your email lists.
Use Cases: Ideal for businesses and individuals looking to find and verify email addresses for outreach campaigns.
Features:
- Email Lookup: Find email addresses and enrich them with additional contact information.
- Enrichment Services: Gain deeper insights into your contacts with social media and company data.
- Gmail/Outlook Integration: Access Clearbit's features directly from your email inbox.
Use Cases: Enhances contact profiles, making it a valuable tool for sales and marketing professionals who use Gmail or Outlook.
Features:
- Email Permutations: Generates potential email address variations based on name and domain.
- Pattern Recognition: Helps identify likely email patterns even when the exact email is unknown.
Use Cases: Useful for guessing email addresses when you know the person’s name and the domain they are associated with.
Features:
- Breach Search: Check if an email address has been exposed in any known data breaches.
- Domain Search: Look for breached accounts associated with a specific domain.
- Notification Services: Get notified if your email appears in future breaches.
Use Cases: Essential for security assessments and ensuring the safety of email addresses.
Features:
- Domain Registration Info: Access the contact details, including email addresses, of domain registrants.
- Historical WHOIS Data: Look up past registration data for investigative purposes.
Use Cases: Great for finding domain owner contact information, useful in domain negotiations or security checks.
Features:
- Compromised Data Search: Search for email addresses within breached databases.
- Keyword Search: Use specific terms to find relevant data breaches.
- Breach Database: Access an extensive database of compromised information.
Use Cases: Ideal for investigators and cybersecurity professionals looking into data breaches and compromised email addresses.
Features:
- Comprehensive Search: Scour multiple databases for email addresses and other personal information.
Use Cases: Best suited for in-depth research across various sources to gather comprehensive data.
Features:
- OSINT Search Engine: Search for email addresses, domains, and associated data across multiple sources.
- Data Aggregation: Combines data from various OSINT sources for thorough intelligence gathering.
Use Cases: Excellent for cybersecurity, investigative journalism, and law enforcement efforts in gathering digital intelligence.
Features:
- Email Verification: Validate email addresses to confirm their validity and deliverability.
- Syntax & Domain Checks: Ensures email addresses are correctly formatted and associated with active domains.
Use Cases: Helps marketers reduce bounce rates by verifying email list accuracy before launching campaigns.
Features:
- Email Validation: Checks the syntax, domain, and mailbox existence of email addresses.
- Bulk Validation: Perform mass verifications for large email lists.
Use Cases: Ensures that email campaigns are launched with accurate, up-to-date email addresses, minimizing errors and improving deliverability rates.
#
Ethical Considerations and Legal Challenges
#
Privacy and Legal Compliance
- GDPR (General Data Protection Regulation): Under GDPR, collecting email addresses, especially from the EU, must comply with strict data protection laws. Always ensure you have consent to use the data.
- CAN-SPAM Act: In the United States, email marketing must comply with the CAN-SPAM Act, which requires transparency in email usage and the option for recipients to unsubscribe.
- Respect for Privacy: Avoid using tools and techniques that infringe on personal privacy. Always consider the ethical implications of the data you collect.
#
Accuracy and Reliability
- Verification: Always verify the accuracy of the email addresses you collect. Tools like Hunter.io, Email Hippo, and Email Checker help ensure the addresses are valid.
- Up-to-Date Information: Email addresses can become obsolete quickly. Regularly update your email lists to maintain accuracy.
#
Ethical Use of Discovered Emails
- Avoid Spam: Never use discovered email addresses for unsolicited communication or spam. This can damage your reputation and result in legal consequences.
- Phishing Risks: Be aware of the potential for phishing if email addresses are misused. Ensure that your use of email addresses is ethical and aligned with legal standards.
#
Security Risks
- Avoid Malicious Activities: The techniques described should not be used for malicious activities such as phishing, spamming, or unauthorized data harvesting.
- Data Breach Sensitivity: If accessing data from breaches or leaks, handle this information with care, respecting the privacy of affected individuals.
#
Password OSINT
Password OSINT (Open Source Intelligence) involves techniques and tools to find, analyze, and secure passwords. This field is essential for identifying vulnerabilities, conducting penetration testing, and enhancing overall security. The following guide provides methods, tools, and ethical considerations for handling password-related information.
#
Techniques for Hunting Breached Passwords
#
Breached Password Databases
Breached password databases are collections of compromised passwords from various data breaches. These databases can be searched to identify if specific passwords have been exposed.
- Features: Provides access to a wide range of data breaches, including email addresses and passwords. Allows keyword and domain searches.
- Use Cases: Useful for discovering if specific credentials have been compromised in known breaches.
- Features: Allows users to check if their passwords have been exposed in recent data breaches. Provides a straightforward search interface.
- Use Cases: Useful for personal security checks and verifying password breaches.
- Features: A comprehensive database of breached passwords and other sensitive information. Offers search capabilities and breach alerts.
- Use Cases: Assists in identifying compromised passwords and monitoring for new breaches.
- Features: A widely recognized service that allows users to check if their email addresses or passwords have been exposed in data breaches. Provides breach notifications and password exposure checks.
- Use Cases: Essential for personal security checks and assessing exposure of specific passwords.
#
Tools for Analyzing and Securing Passwords
#
Password Strength Checkers
- Features: Provides a searchable database of compromised passwords. Users can check if their passwords have been exposed in breaches.
- Use Cases: Helps in determining the strength of passwords and assessing their exposure risk.
- Features: Generates strong, random passwords for use in securing accounts. Allows customization of password length and complexity.
- Use Cases: Ideal for creating secure passwords that are less likely to be compromised.
#
Password Cracking Tools
These tools are used to test the strength of passwords by attempting to crack them using various techniques.
- Features: A powerful password recovery tool that supports multiple hashing algorithms. Uses techniques like brute force, dictionary attacks, and rule-based attacks.
- Use Cases: Useful for penetration testers and security professionals assessing password strength.
- Features: An open-source password cracking tool that supports various hashing algorithms and attack methods. Includes features for dictionary and brute force attacks.
- Use Cases: Commonly used in security assessments and forensic investigations.
This Blog Continues Coming Soon
Stay tuned for the next update. We are working on new content and will be publishing more information soon. Check back regularly for the latest posts and updates!
